How Can You Protect Your Home Computer – Cyber Awareness 2025
The home computer is now more than just a personal gadget in our digitally connected world; it’s a doorway to your online life. In 2025, safeguarding your home computer is more important than ever due to the growth of cloud-based services, online learning, remote employment, and smart homes. Cybercriminals are always changing their strategies, use social engineering, artificial intelligence, and sophisticated malware to take advantage of flaws in software, systems, and even human behavior. Cyber awareness is a required mindset, not just a trendy term. Everything you need to know to keep your home computer safe in 2025 will be covered in this blog post, from basic security procedures to sophisticated defense tactics.
1. Keep Your Software Updated
Unpatched software is one of the most popular methods hackers get onto household computers. Updates are frequently released by developers to address security flaws, but if you choose not to install them, your computer becomes a prime target. Best practices include:
> Enabling automatic operating system updates.
> Frequently updating third-party software (such as Zoom, Adobe, and browsers).
> Maintaining drivers and firmware (particularly for routers and Internet of Things devices) up to date. Advice: If you would rather install updates by hand, set a weekly reminder to check for them.
2. Use a Comprehensive Security Suite
Traditional antiviral software is insufficient in 2025. You require a contemporary cybersecurity package that consists of:
> Web filtering;
> Firewall protection;
> Ransomware protection;
> VPN for safe browsing;
> Antivirus and anti-malware software.
AI is used by several solutions to quickly identify and address new dangers, including ones that have never been seen before. Bitdefender, Norton 360, Kaspersky, McAfee, and Malwarebytes Premium are well-liked choices.
3. Strengthen Your Password Game
One of the biggest threats to cybersecurity is using weak and frequently used passwords. Credential stuffing attacks, in which hackers attempt to access multiple websites using credentials they have acquired from one breach, are common, and password cracking tools have advanced significantly. Do the following:
> Create strong, one-of-a-kind passwords for each account;
> Use a combination of capital, lowercase, numbers, and symbols;
> Steer clear of dictionary phrases and private information (birthdays, pet names).
Pro Tip: To create and save complicated passwords, use a password manager such as Bit warden, 1Password, or LastPass. Nowadays, several provide breach monitoring and notifications in the event that your credentials are compromised.
4. Enable Multi-Factor Authentication (MFA)
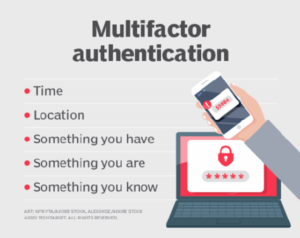
Passwords by themselves cannot ensure security. By requiring a second verification method, multi-factor authentication (MFA), sometimes referred to as two-factor authentication (2FA), offers an additional layer of security. MFA types include:
> Verification codes sent by email or SMS Apps for authenticators (such as Authy or Google Authenticator);
> hardware tokens (such as YubiKey); and biometrics (such as face recognition or fingerprints)
> Apply MFA to the following: social networking; cloud storage (Google Drive, OneDrive, Dropbox); email accounts; online banking; and remote work tools.
5. Secure Your Home Wi-Fi Network
The gateway to your digital world is your home Wi-Fi. If it’s not secure, hackers can access network-connected devices, steal data, and spy on your activity. To encrypt your Wi-Fi, follow these steps:
> Modify the router’s default username and password. > Employ WPA3 encryption (or, in the event that WPA3 is unavailable, WPA2).
> Turn off WiFi Protected Setup, or WPS, as it is susceptible to brute-force attacks.
> Establish a guest network for guests and Internet of Things gadgets.
> Update the firmware on your router on a regular basis.
> If you wish to add even more secrecy, hide your SSID.
Bonus Tip: Real-time threat monitoring and integrated network security are features of some more recent routers.
6. Beware of Phishing and Social Engineering
Phishing assaults have changed significantly over time. These days, they can be found through messaging applications, voice calls (vishing), text messages (smishing), deepfake videos, and even artificial intelligence (AI)-generated sounds in 2025. How to keep oneself safe:
> Always double-check the sender’s identity, especially when dealing with sensitive or money-related requests; > Never click on dubious links or attachments. Examine URLs carefully because lookalike domains are frequently used by phishers.
> To identify phishing attempts, use browser addons such as u Block Origin or Net craft.
> Advice: A lot of contemporary email systems report alleged phishing attempts. Be mindful of cautions.
7. Back Up Your Data—Religiously
Regular backups might safeguard your digital life in the age of ransomware. Having a solid backup plan guarantees that you can recover your data in the event that your device is stolen, misplaced, or infected with malware. Observe the 3-2-1 backup guideline:
> Maintain three copies of your data.
> Keep one copy offshore (on the cloud or in a safe place);
> Keep it on two separate kinds of media (for example, cloud + external hard drive).
> The best backup programs are Acronis True Image, Back blaze, IDrive, and integrated programs like macOS Time Machine and Windows File History.
8. Use Standard User Accounts, Not Admin
Any implanted malware has complete access over your system when you run it as an administrator. Use a regular user account instead, and only go into admin mode when absolutely required. This lessens the harm in the event that malware attempts to install apps or change system settings.
9. Secure Your Internet of Things (IoT) Devices
In 2025, homes are filled with smart devices—TVs, fridges, cameras, thermostats, lights, and even door locks. Each one is a potential entry point for attackers.
Tips for securing IoT:
> Change default usernames and passwords.
> Keep firmware updated.
> Disable unused features like remote access.
> Place IoT devices on a separate network or VLAN.
> Use devices from reputable brands that offer ongoing security support.
10. Enable a DNS Filter
Before harmful websites load, they are blocked by a DNS filtering service. It functions similarly to a bouncer that examines each page you visit. The best DNS filters include Next DNS, Cloudflare for Families, Clean Browsing, and OpenDNS. These services are particularly helpful if you wish to stay away from hazardous or adult content or if you have children at home.
11. Lock Your Devices When Not in Use
Although it may seem simple, it’s simple to forget. Even at home, always lock your screen before leaving your computer. Make use of brief timeouts and automatic screen locks. Bonus: Configure your device to start up requiring a password, PIN, or biometric login.
12. Practice Digital Hygiene
Cybersecurity is as much about behavior as it is about tools. Teach everyone in your home good digital hygiene.
Develop the following habits:
> Avoid downloading from unreliable sources;
> Avoid connecting unknown USB drives.
> Clear your browser’s cache and cookies on a regular basis.
> Do not use unprotected public Wi-Fi.
> When you’re done, log out of your accounts.

Educate your family—especially kids and elderly relatives—about online threats and safe browsing practices.
13. Monitor for Breaches and Identity Theft
Data breaches can occur despite the greatest practices. Make use of services that keep an eye out for personal data leaks on the dark web.
Useful tools:
> Have I Been Pwned (free)
> Identity Guard
> LifeLock
> Aura
> Password managers with breach alerts
If your info has been leaked, immediately change the associated password and enable MFA.
14. Use a VPN for Privacy and Protection
A Virtual Private Network (VPN) shields you from some online tracking and protects you when using public Wi-Fi by encrypting your internet traffic and hiding your IP address.
VPNs are especially useful if you:
> Work remotely
> Use public Wi-Fi often
> Want to access geo-blocked content
> Value online anonymity
Top VPNs in 2025: NordVPN, ExpressVPN, Surfshark, ProtonVPN, and CyberGhost.

15. Keep an Eye on Emerging Threats
Cyberthreats are always changing. Subscribe to reliable cybersecurity newsletters, podcasts, and blogs to stay informed.
Recommended sources:
> Krebs on Security
> The Hacker News
> CyberScoop
> Threatpost
> US-CERT alerts
Staying informed helps you anticipate new threats and adjust your defenses accordingly.
Final Thoughts:
Build a Cybersecurity Mindset
Vigilance, consistency, and wise practices are key components of cyber awareness in 2025. Software and tools are essential, but they only function well when used. In cybersecurity, users, not devices, are frequently the weakest link.
By following these practices, you’re not just protecting a machine—you’re safeguarding your digital identity, finances, memories, and the well-being of your household.
Remember: Cybersecurity isn’t a one-time setup. It’s a lifestyle.

Quick Checklist for Cyber-Savvy Homes in 2025:
* OS and software auto-updated
* Modern antivirus installed
* Strong, unique passwords in a password manager
* MFA enabled on all accounts
* Secure Wi-Fi with WPA3
* Regular data backups
* Router and IoT devices updated and segmented
* DNS filtering active
* Devices locked and users trained